Ubikom is a digital ID registry, and its utility goes well beyond email. Below are some examples of possible applications.
Your baby monitor, security camera, or smart thermostat must have safe and reliable online representation. Ubikom protocol removes the need for a hodgepodge of firmware and standardizes interaction with and between objects. This protects the IoT from being hacked through weak links, which may be present anywhere: lax security of your "smart" refrigerator's or vacuum cleaner's connectivity can allow thieves to take over your network, and compromise security of your house.
Using Ubikom's ID registry, it is easy to build fully secure connection protocols, and test them to a very high standard. This will ensure universal robust security.
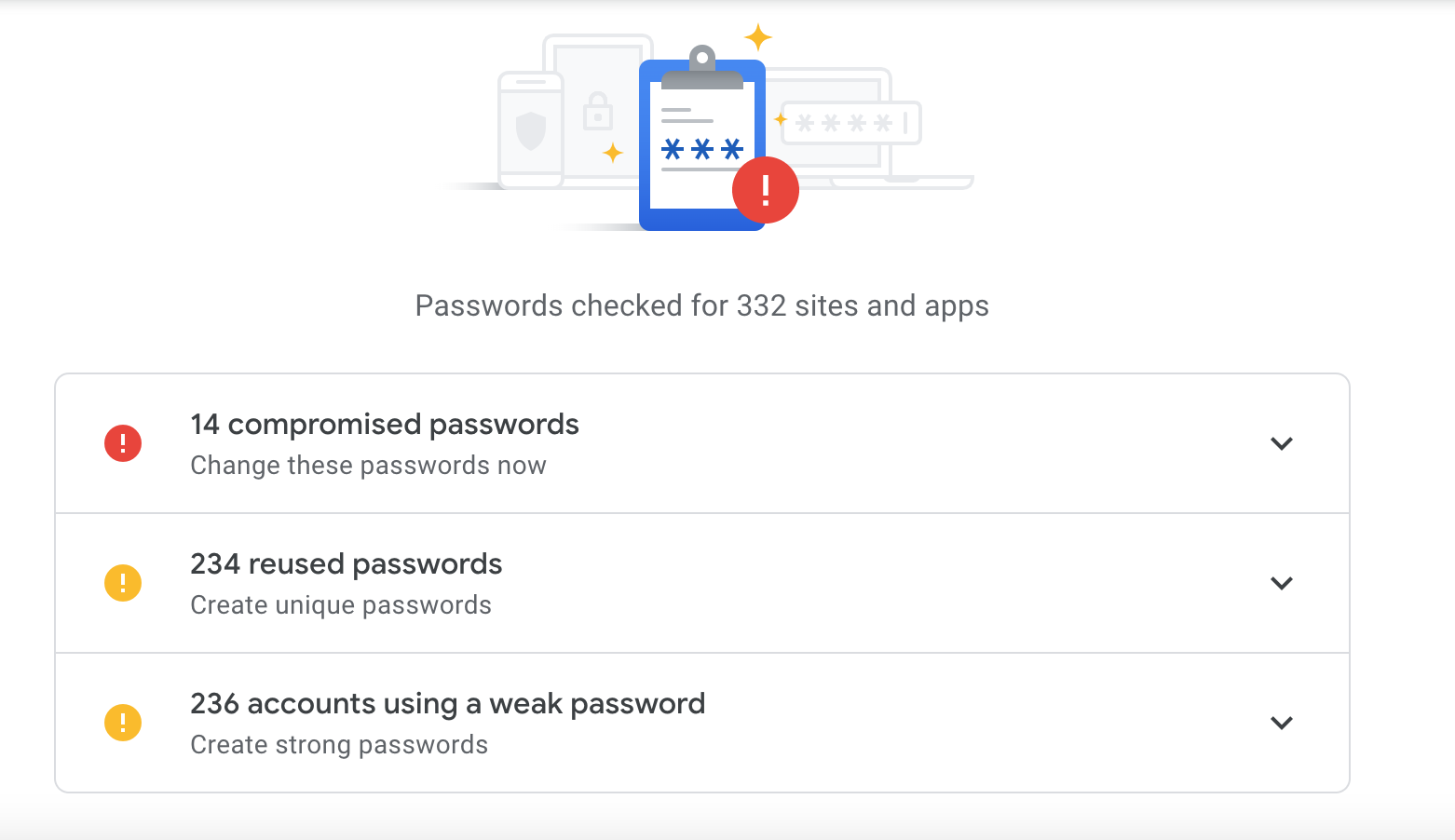
Today, I have passwords saved in my keychain, in my google account, and in my password manager. Keeping them synced is rather involved. Besides, I have many old passwords accumulated over several years, and some of them are not very robust. Perhaps a more organized person would keep it all tidy, but this requires constant attention. I believe that the warnings shown below are typical for many of us.

Now imagine that you signed up with your ubikom avatar instead. No passwords need to be kept anywhere: thanks to public key cryptography, you and only you can authenticate yourself as the owner of this avatar and therefore the owner of the purchase. Even if the seller’s server is hacked, nothing of interest is leaked - your avatar is not a secret.