Email is a convenient, cheap, and powerful way of communication. It is one of the first successful applications of the nascent, late 20th century internet. It is ubiquitous and unassuming. Why improve it?
Email was invented in a different era. Its first users were scientists who liked working in broad collaboration. They appreciated email’s ability to connect them to colleagues around the world. This was before the advent of spam, phishing, targeted ads, snooping, and other problem children of the internet. Email was not designed to be secure, or particularly private. Its creators did not anticipate that email would become the most ubiquitous form of communication, thus inviting spying, censorship, abuse, theft, and other attendant human ills.
Now, more than 30 years since its use became widespread, email is neither safe, nor private, nor belongs to its users - sending confidential messages is difficult; it is owned by giant corporations, which are reading emails to send us ads and can block or close our accounts; data privacy is not protected (companies owning email services not only are snooping on us, but they can respond to a government’s requests to share their users’ data); it is so easy for oppressive government to read email traffic, that no dissident would think about using email.
Most of us do not give much thought to these concerns, until we face consequences of our nonchalant attitude. My Outlook account was blocked because calendar went crazy. For a few days my main personal account was inaccessible. And everyone has an identity theft story to share, especially if you have ageing parents who are targeted by scumbags.
Can we make email truly confidential and secure, while keeping its convenience and low cost? (Even though most of us don’t pay for email, we are paying indirectly by letting companies glean valuable data from our “private” communications.)
The problem of confidentiality of communication has been solved by the invention of public key cryptography. If we want to receive a confidential message, the sender needs to obtain our public key, which a long string of numbers. The public key locks the protective envelope of the sent message. We own—and keep safely on our personal device—the corresponding private key that unlocks the envelope. It is computationally unfeasible for anyone to open the envelope without the private key. This technology underlies internet security.
However, it is difficult to keep the protocol convenient and robust. Solutions such as S/MIME rely on centralized certificate authorities and are very hard to configure and use. The standard centralized public key infrastructure (PKI) required for this protocol is unwieldy.
We make it easy to create and register names with the corresponding cryptographic keys. These names are freely chosen by users and are , rather than real IDs. The avatars belong to us, the users who created them, rather than to giant corporations dominating our digital lives. Avatars are recorded on a public blockchain and freely accessible by anyone. Protected by blockchain technology, avatars are safe from bans or deletions: no one can cancel or ban us from our accounts, since no one owns access to them. Since avatars are freely chosen by users and not tied to real identities, Ubikom avoids the bureaucratic obstacles plaguing Self-Sovereign Identity (SSI)
Here’s an interesting side effect—if you are encrypting all the outgoing data, it becomes less important how exactly your message is delivered to the recipient. Safe delivery channels are very important for regular, un-encrypted, email (recall any of the leaked email scandals). But if your email is encrypted, you don’t care if it is intercepted—no one will be able to read it anyway. For everyone but you, your email is just a bunch of meaningless bytes.
Ubikom users can exchange emails with accounts outside of Ubikom, of course. However, since emails in legacy systems are not encrypted, we must decrypt emails when they leave the Ubikom’s perimeter. The more people join Ubikom, the more secure is everyone's email.
Ubikom avatars are registered on a blockchain. Today, blockchains are firmly associated with digital currencies. For us, however, registration on the blockchain must remain cheap for the service to remain affordable or free for personal use. For this and other reasons we are creating own blockchain for the ID registry. Early participants will receive , the tokens of this blockchain.
Any messaging platform must uniquely identify senders and recipients and guarantee faithful delivery. We can break this task into three parts:
A better way to create a public encryption utility is to have a unique cryptographic key pair assigned to each user. Every sent message will be signed by the private key and verified using the public key. The problem of the user identification is reduced to the control of the private key.
When a message is received, we need assurance that came from the declared source. This is typically accomplished by using Private Key Infrastructure (PKI). All messages are signed with the senders' private keys. Using PKI, we can also encrypt data with a key derived from the sender's private key and the recipient’s public key. In this way, the message's provenance and authenticity is established, and only the intended recipient can decrypt it.
Finally, addressing users by their public keys works well for machines but not for humans. We prefer short names that are easy to remember, so we might want to create a registry to keep such names and the corresponding keys. But we must make sure that such a registry does not become the central authority that we seek to avoid.
These ideas led to the creation of Ubikom, the registry of digital avatars. The diagrams below explain Ubikom‘s protocol for sending and receiving emails, which are end-to-end encrypted by design.
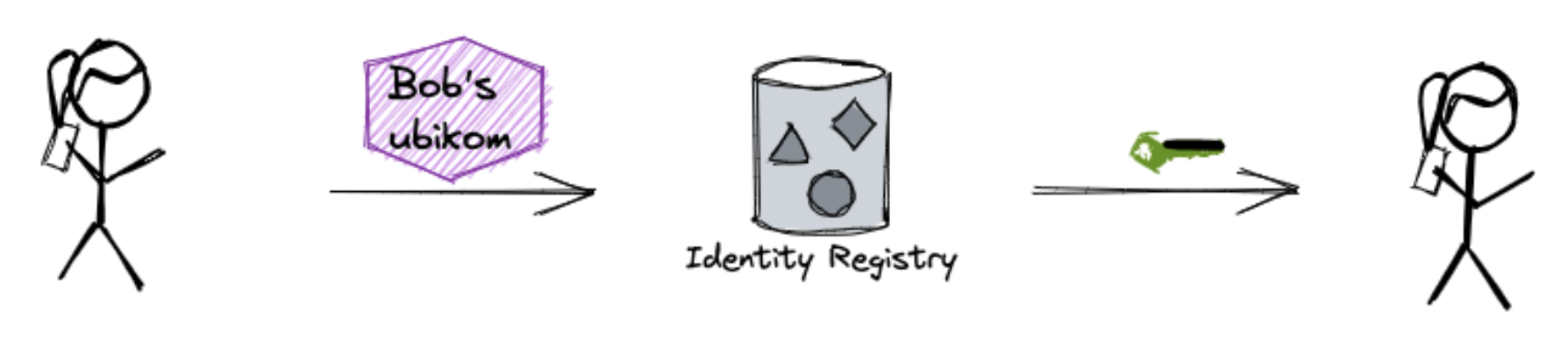
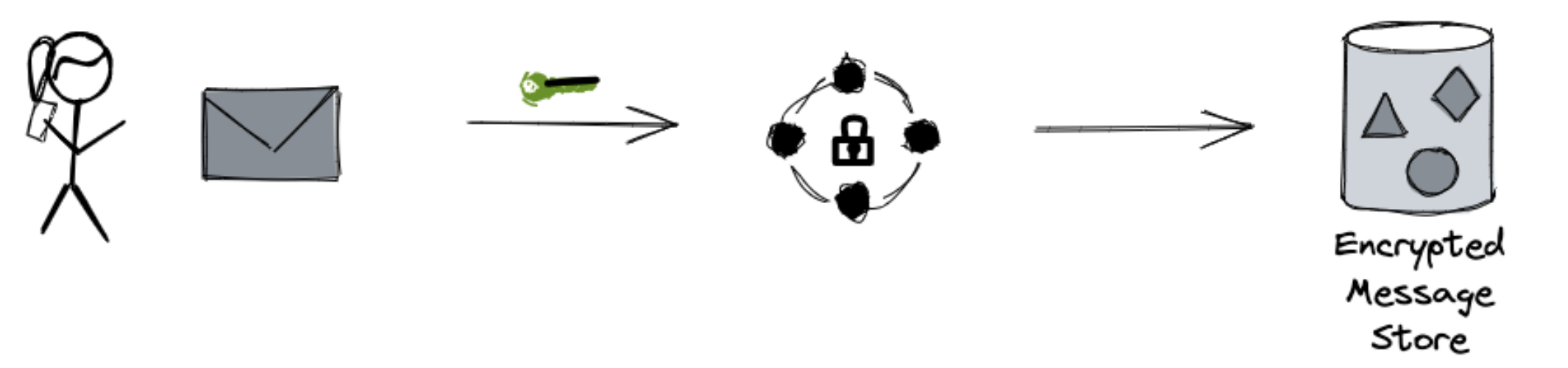
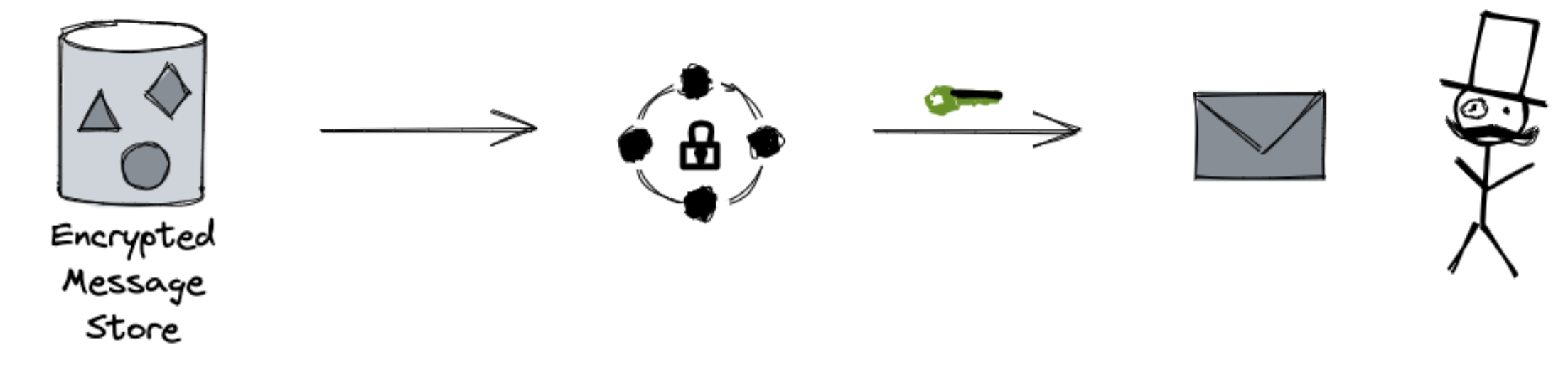
As you can see, only encrypted messages are ever sent via public network.
If you are interested to learn more technical details, please read on.
Ubikom email is up and running. While work is still in progress, you can create your avatar and start using secure email. You can install it on your device and/or access it through webmail. Get your account here: ubikom.cc.